★更新予定
Aws/CloudFormation/2.Knowhow
00_ネストスタック構成
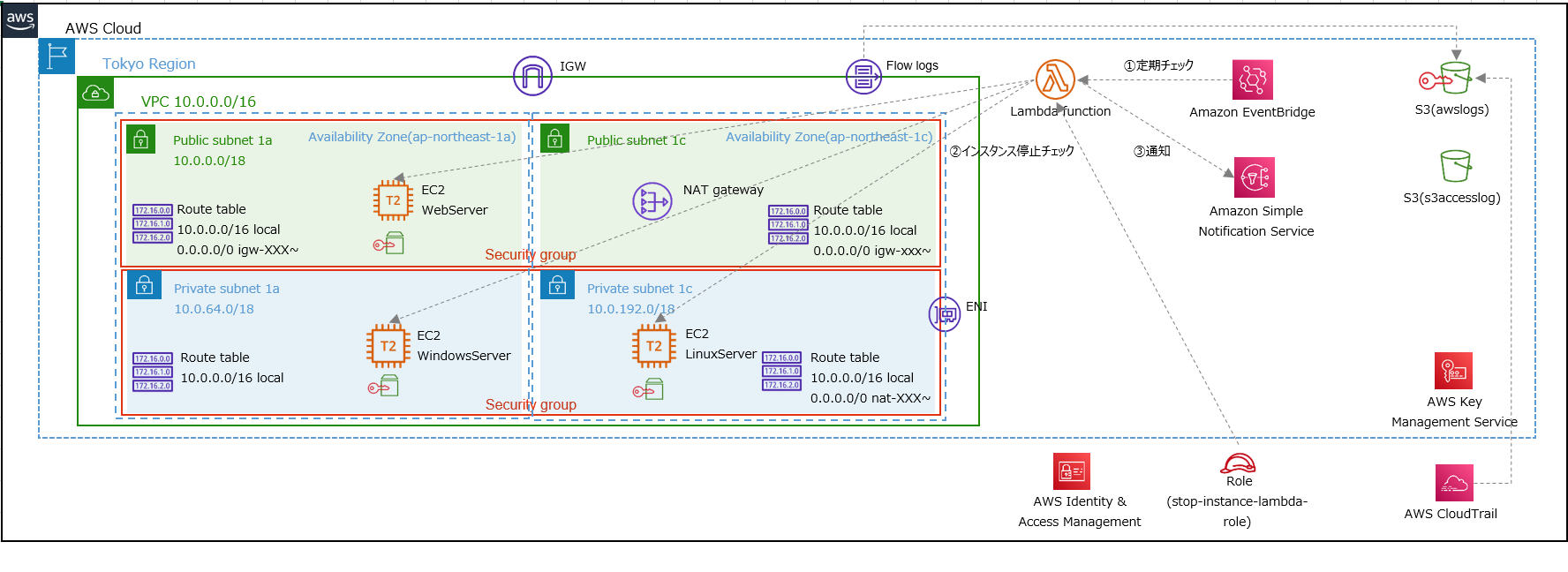
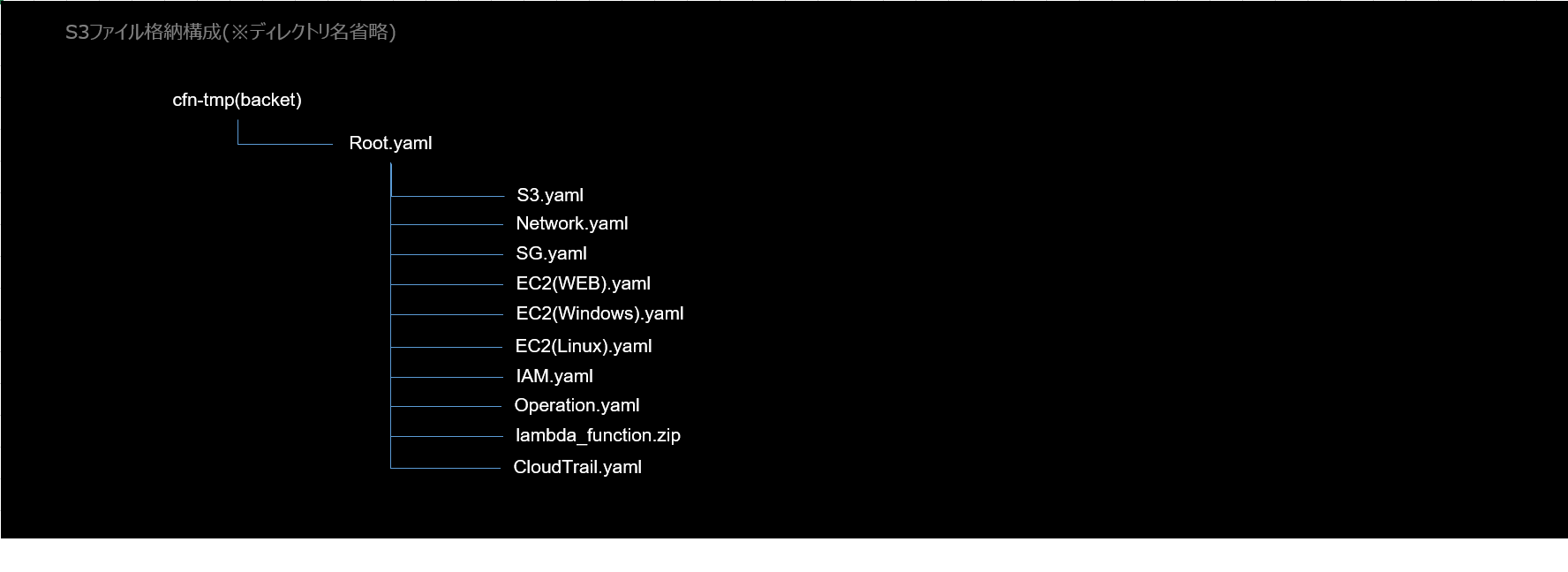
- Root.yaml
- 更新予定
- S3.yaml
-

AWSTemplateFormatVersion: 2010-09-09 Description: Provision S3 Parameters: HeadName: Type: String Default: cfn Resources: # ------------------------------------------------------------ # # AWS-Logs(VPCFlowLog,ClouTrail) # # ------------------------------------------------------------ # AWSLogs: Type: AWS::S3::Bucket Properties: BucketName: !Sub ${HeadName}-awslogs AccessControl: LogDeliveryWrite PublicAccessBlockConfiguration: BlockPublicAcls: false BlockPublicPolicy: false IgnorePublicAcls: false RestrictPublicBuckets: false BucketEncryption: ServerSideEncryptionConfiguration: - ServerSideEncryptionByDefault: SSEAlgorithm: AES256 LoggingConfiguration: DestinationBucketName: !Sub ${HeadName}-s3accesslog LogFilePrefix: awslogs/ LifecycleConfiguration: Rules: - Id: !Sub ${HeadName}-s3accesslog-lifecycle-rule Status: Enabled ExpirationInDays: 365 Transitions: - StorageClass: GLACIER TransitionInDays: 30 Tags: - Key: Name Value: !Sub ${HeadName}-awslogs AWSLogsPolicy: Type: AWS::S3::BucketPolicy DependsOn: AWSLogs Properties: Bucket: !Ref AWSLogs PolicyDocument: Version: 2012-10-17 Statement: - Sid: AWSCloudTrailAclCheck Effect: Allow Principal: Service: - cloudtrail.amazonaws.com Action: s3:GetBucketAcl Resource: !GetAtt AWSLogs.Arn - Sid: AWSCloudTrailWrite Effect: Allow Principal: Service: - cloudtrail.amazonaws.com Action: s3:PutObject Resource: !Join [ '', [ !GetAtt AWSLogs.Arn, '/AWSLogs/', !Ref 'AWS::AccountId', '/*' ] ] Condition: StringEquals: s3:x-amz-acl: bucket-owner-full-control # ------------------------------------------------------------ # # S3-AccessLog # # ------------------------------------------------------------ # S3AccessLog: Type: AWS::S3::Bucket Properties: BucketName: !Sub ${HeadName}-s3accesslog AccessControl: LogDeliveryWrite PublicAccessBlockConfiguration: BlockPublicAcls: false BlockPublicPolicy: false IgnorePublicAcls: false RestrictPublicBuckets: false BucketEncryption: ServerSideEncryptionConfiguration: - ServerSideEncryptionByDefault: SSEAlgorithm: AES256 LoggingConfiguration: DestinationBucketName: !Sub ${HeadName}-s3accesslog LogFilePrefix: s3/ LifecycleConfiguration: Rules: - Id: !Sub ${HeadName}-s3accesslog-lifecycle-rule Status: Enabled ExpirationInDays: 365 Transitions: - StorageClass: GLACIER TransitionInDays: 30 Tags: - Key: Name Value: !Sub ${HeadName}-s3accesslog Outputs: S3BacketId: Value: !GetAtt AWSLogs.Arn Export: Name: UseAWSLogs S3BacketName: Value: !Ref AWSLogs Export: Name: UseS3BacketName
- Network.yaml
-
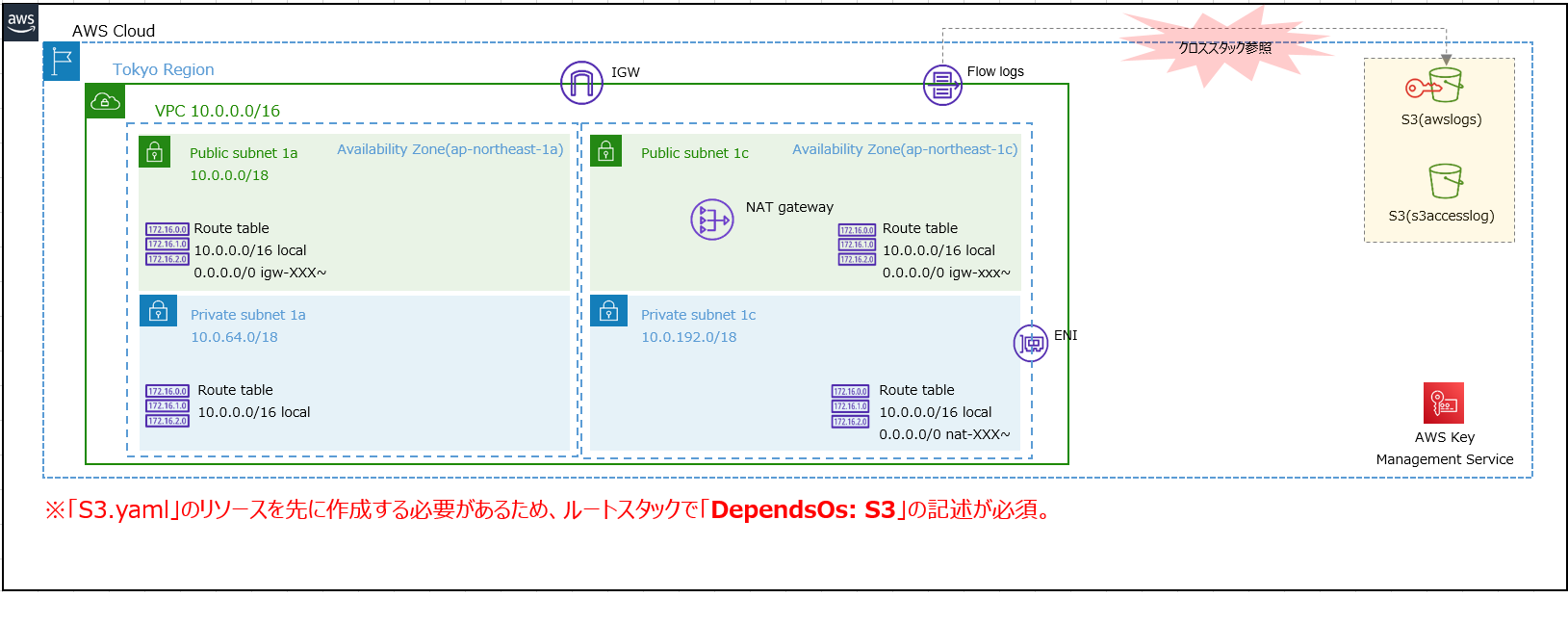
AWSTemplateFormatVersion: 2010-09-09 Description: Provision Network Architecture Parameters: HeadName: Type: String Default: cfn CidrBlock: Type: String Default: 10.0.0.0/16 Internet: Type: String Default: 0.0.0.0/0 Resources: # ------------------------------------------------------------ # # VPC # # ------------------------------------------------------------ # VPC: Type: AWS::EC2::VPC Properties: CidrBlock: !Ref CidrBlock EnableDnsHostnames: true EnableDnsSupport: true InstanceTenancy: default Tags: - Key: Name Value: !Sub ${HeadName}-vpc VPCFlowLogs: Type: AWS::EC2::FlowLog DependsOn: VPC Properties: LogDestination: !ImportValue UseAWSLogs LogDestinationType: s3 ResourceId: !Ref VPC ResourceType: VPC TrafficType: ALL Tags: - Key: Name Value: !Sub ${HeadName}-vpcflowlogs # ------------------------------------------------------------ # # IGW # # ------------------------------------------------------------ # IGW: Type: AWS::EC2::InternetGateway Properties: Tags: - Key: Name Value: !Sub ${HeadName}-igw # ------------------------------------------------------------ # # VPC-IGW Attachment # # ------------------------------------------------------------ # VPCIGWAttachment: Type: AWS::EC2::VPCGatewayAttachment Properties: VpcId: !Ref VPC InternetGatewayId: !Ref IGW # ------------------------------------------------------------ # # PublicSubnet # # ------------------------------------------------------------ # PublicSubnet1a: Type: AWS::EC2::Subnet DependsOn: VPCIGWAttachment Properties: VpcId: !Ref VPC AvailabilityZone: !Sub ${AWS::Region}a CidrBlock: !Select [0, !Cidr [!GetAtt VPC.CidrBlock, 1, 14]] MapPublicIpOnLaunch: true Tags: - Key: Name Value: !Sub ${HeadName}-pbsbn1a PublicSubnet1c: Type: AWS::EC2::Subnet DependsOn: VPCIGWAttachment Properties: VpcId: !Ref VPC AvailabilityZone: !Sub ${AWS::Region}c CidrBlock: !Select [2, !Cidr [!GetAtt VPC.CidrBlock, 3, 14]] MapPublicIpOnLaunch: true Tags: - Key: Name Value: !Sub ${HeadName}-pbsbn1c # ------------------------------------------------------------ # # PrivateSubnet # # ------------------------------------------------------------ # PrivateSubnet1a: Type: AWS::EC2::Subnet DependsOn: VPCIGWAttachment Properties: VpcId: !Ref VPC AvailabilityZone: !Sub ${AWS::Region}a CidrBlock: !Select [1, !Cidr [!GetAtt VPC.CidrBlock, 2, 14]] MapPublicIpOnLaunch: false Tags: - Key: Name Value: !Sub ${HeadName}-pvsbn1a PrivateSubnet1c: Type: AWS::EC2::Subnet DependsOn: VPCIGWAttachment Properties: VpcId: !Ref VPC AvailabilityZone: !Sub ${AWS::Region}c CidrBlock: !Select [3, !Cidr [!GetAtt VPC.CidrBlock, 4, 14]] MapPublicIpOnLaunch: false Tags: - Key: Name Value: !Sub ${HeadName}-pvsbn1c # ------------------------------------------------------------ # # NGW # # ------------------------------------------------------------ # NGW: Type: AWS::EC2::NatGateway Properties: AllocationId: !GetAtt EIP.AllocationId ConnectivityType: public SubnetId: !Ref PublicSubnet1c Tags: - Key: Name Value: !Sub ${HeadName}-ngw # ------------------------------------------------------------ # # EIP # # ------------------------------------------------------------ # EIP: Type: AWS::EC2::EIP DependsOn: VPCIGWAttachment Properties: Domain: vpc Tags: - Key: Name Value: !Sub ${HeadName}-eip # ------------------------------------------------------------ # # RouteTable # # ------------------------------------------------------------ # PublicSubnet1aRouteTable: Type: AWS::EC2::RouteTable Properties: VpcId: !Ref VPC Tags: - Key: Name Value: !Sub ${HeadName}-pbsbn1a-rt PublicSubnet1cRouteTable: Type: AWS::EC2::RouteTable Properties: VpcId: !Ref VPC Tags: - Key: Name Value: !Sub ${HeadName}-pbsbn1c-rt PrivateSubnet1aRouteTable: Type: AWS::EC2::RouteTable Properties: VpcId: !Ref VPC Tags: - Key: Name Value: !Sub ${HeadName}-pvsbn1a-rt PrivateSubnet1cRouteTable: Type: AWS::EC2::RouteTable Properties: VpcId: !Ref VPC Tags: - Key: Name Value: !Sub ${HeadName}-pvsbn1c-rt # ------------------------------------------------------------ # # Routing(IGW,NGW) # # ------------------------------------------------------------ # PublicSubnet1aIGWRoute: Type: AWS::EC2::Route Properties: RouteTableId: !Ref PublicSubnet1aRouteTable DestinationCidrBlock: !Ref Internet GatewayId: !Ref IGW PublicSubnet1cIGWRoute: Type: AWS::EC2::Route Properties: RouteTableId: !Ref PublicSubnet1cRouteTable DestinationCidrBlock: !Ref Internet GatewayId: !Ref IGW PrivateSubnet1cNGWRoute: Type: AWS::EC2::Route Properties: RouteTableId: !Ref PrivateSubnet1cRouteTable DestinationCidrBlock: !Ref Internet NatGatewayId: !Ref NGW # ------------------------------------------------------------ # # RouteTable Associate # # ------------------------------------------------------------ # PublicSubnet1aRouteTableAssociation: Type: AWS::EC2::SubnetRouteTableAssociation Properties: SubnetId: !Ref PublicSubnet1a RouteTableId: !Ref PublicSubnet1aRouteTable PublicSubnet1cRouteTableAssociation: Type: AWS::EC2::SubnetRouteTableAssociation Properties: SubnetId: !Ref PublicSubnet1c RouteTableId: !Ref PublicSubnet1cRouteTable PrivateSubnet1aRouteTableAssociation: Type: AWS::EC2::SubnetRouteTableAssociation Properties: SubnetId: !Ref PrivateSubnet1a RouteTableId: !Ref PrivateSubnet1aRouteTable PrivateSubnet1cRouteTableAssociation: Type: AWS::EC2::SubnetRouteTableAssociation Properties: SubnetId: !Ref PrivateSubnet1c RouteTableId: !Ref PrivateSubnet1cRouteTable Outputs: VPCId: Value: !Ref VPC Export: Name: UseVPC IGWId: Value: !Ref IGW Export: Name: UseIGW PublicSubnet1aId: Value: !Ref PublicSubnet1a Export: Name: UsePublicSubnet1a PublicSubnet1cId: Value: !Ref PublicSubnet1c Export: Name: UsePublicSubnet1c PrivateSubnet1aId: Value: !Ref PrivateSubnet1a Export: Name: UsePrivateSubnet1a PrivateSubnet1cId: Value: !Ref PrivateSubnet1c Export: Name: UsePrivateSubnet1c
# エラー履歴
- CFnテンプレート内でLambda環境変数(複数インスタンスID)指定したけど上手く取れない?
-
■ 実現したいこと
別々のCFnテンプレートでEC2とLambdaをそれぞれリソース作成。
EC2作成時にインスタンスIDの値を動的に取得および出力し、
Lambda作成時に↑で取得したインスタンスIDの値を参照し環境変数を登録する。
↑で登録した対象インスタンスを自動停止させたい。
■ 事象
(1)CFnテンプレート内にて、以下Lambda環境変数(複数インスタンスID)について記載。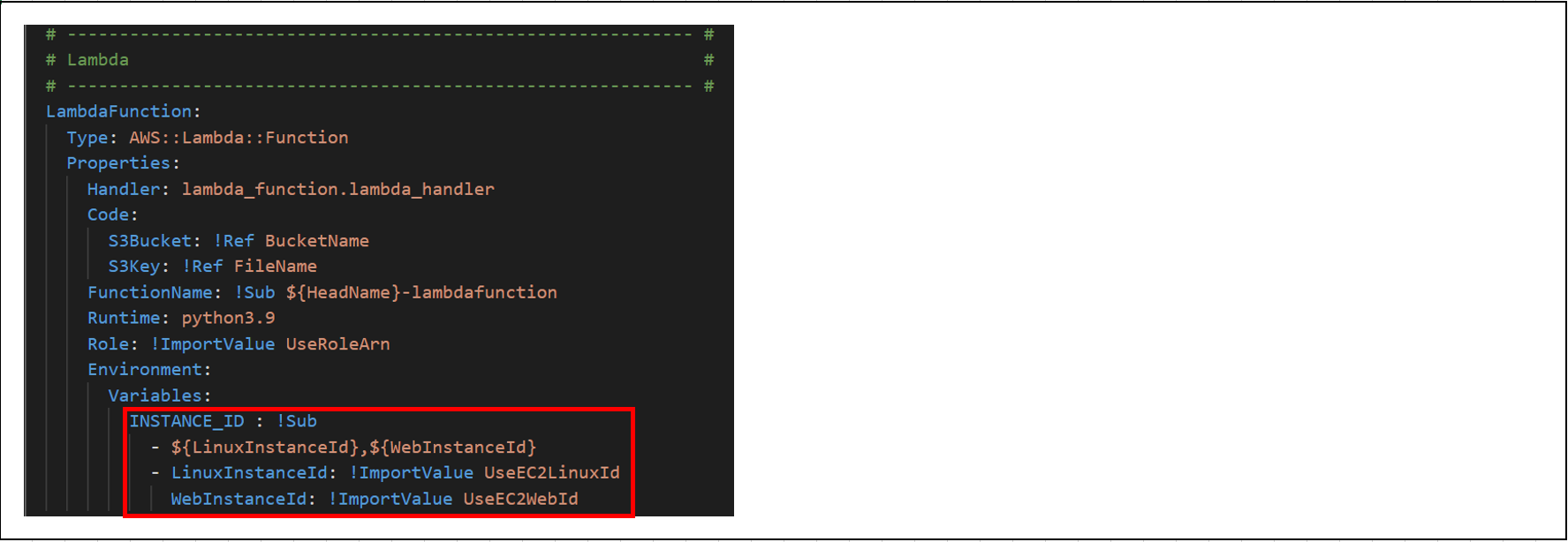
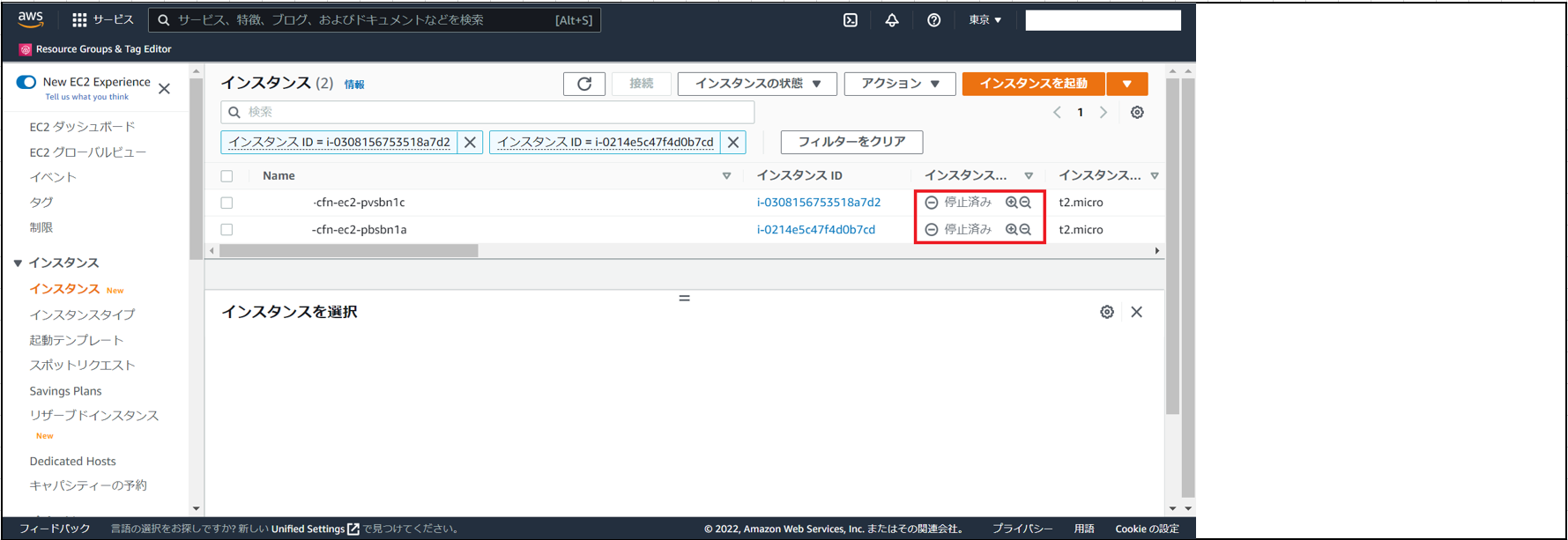
(2)スタックを作成後、EC2へアクセスし、インスタンスが作成されていることを確認。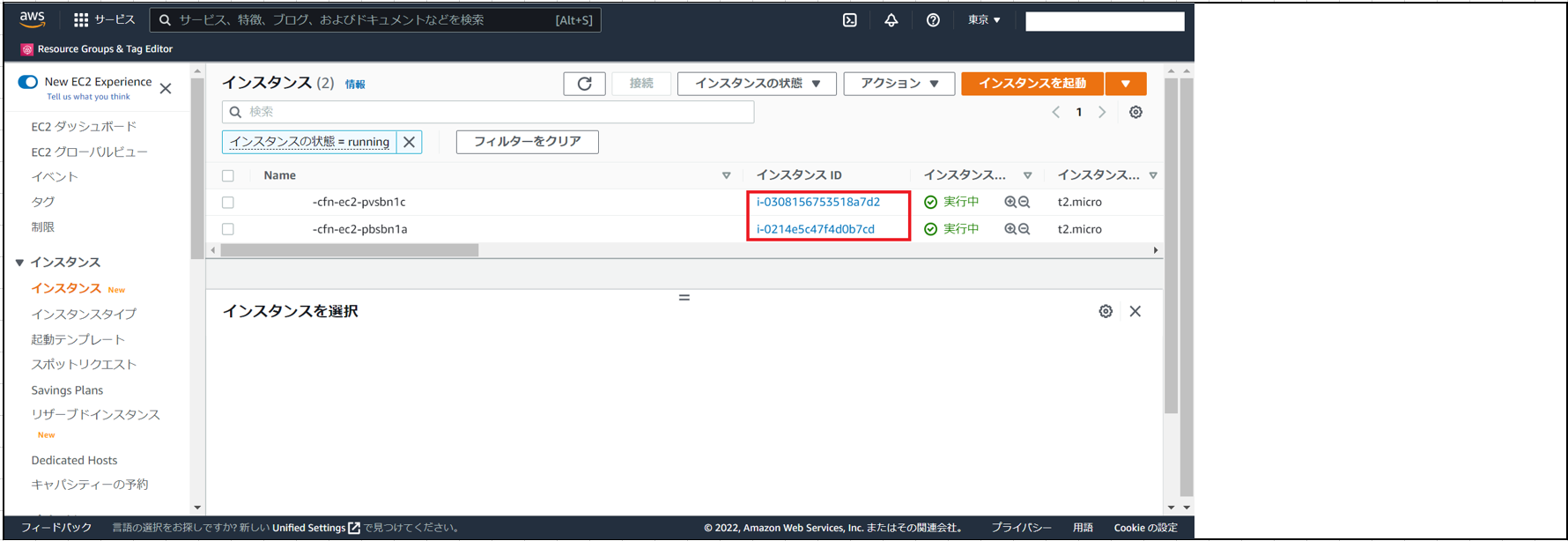
(3)Lambdaへアクセスし、↑で確認したインスタンスと同様のインスタンスIDがLambda環境変数に登録されていることを確認。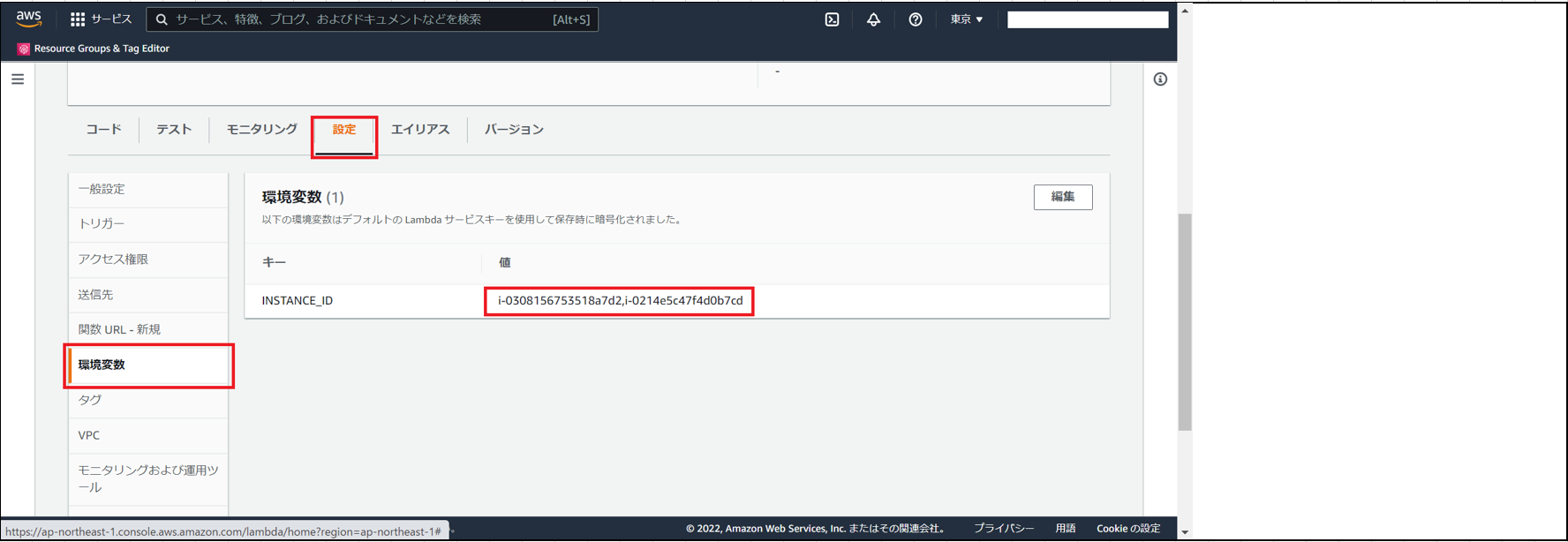
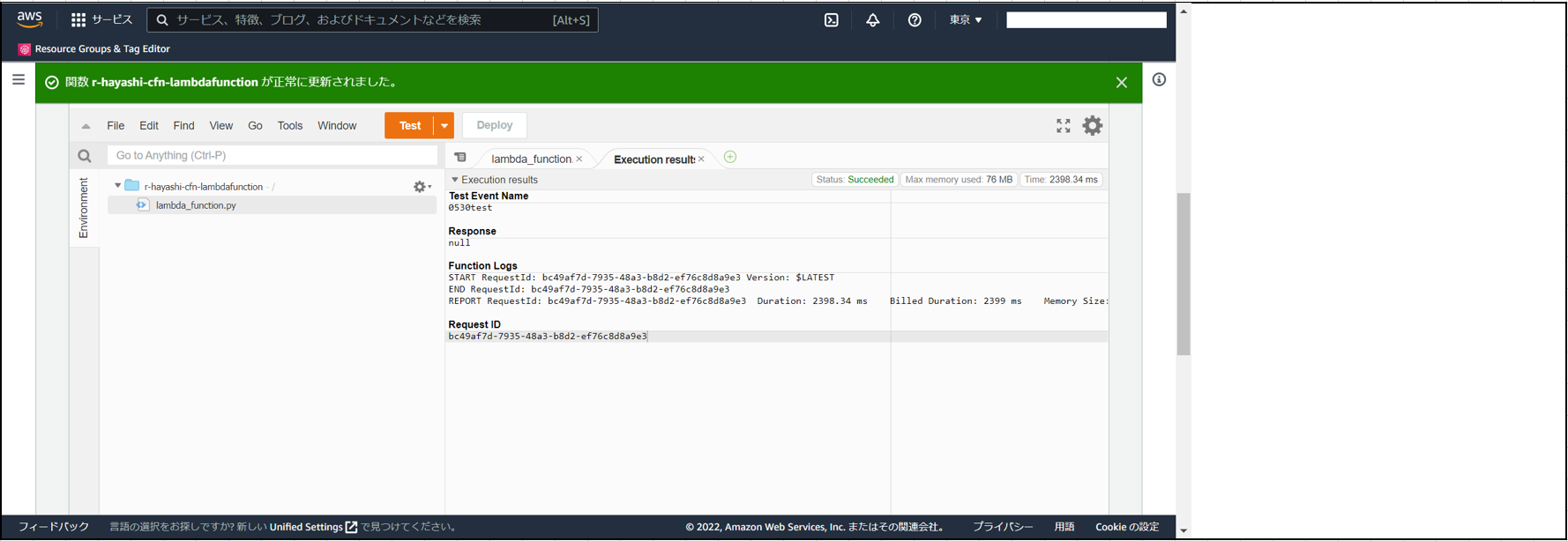
(4)「Test」を押下。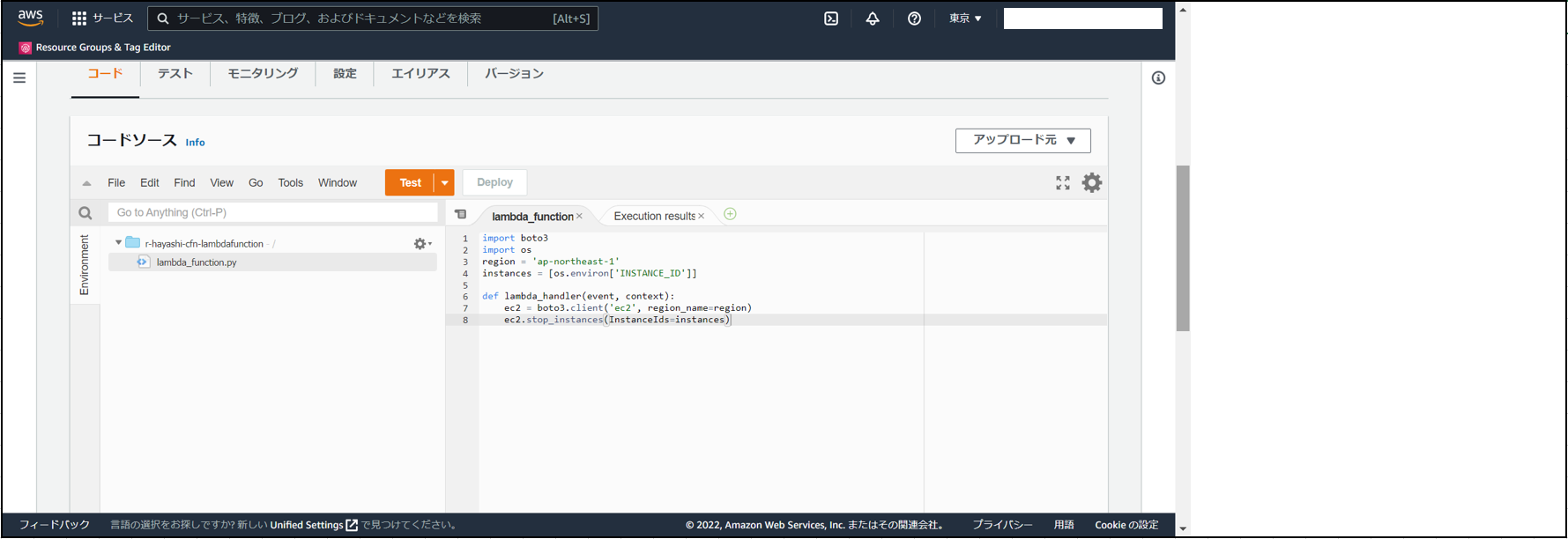
(5)エラー発生。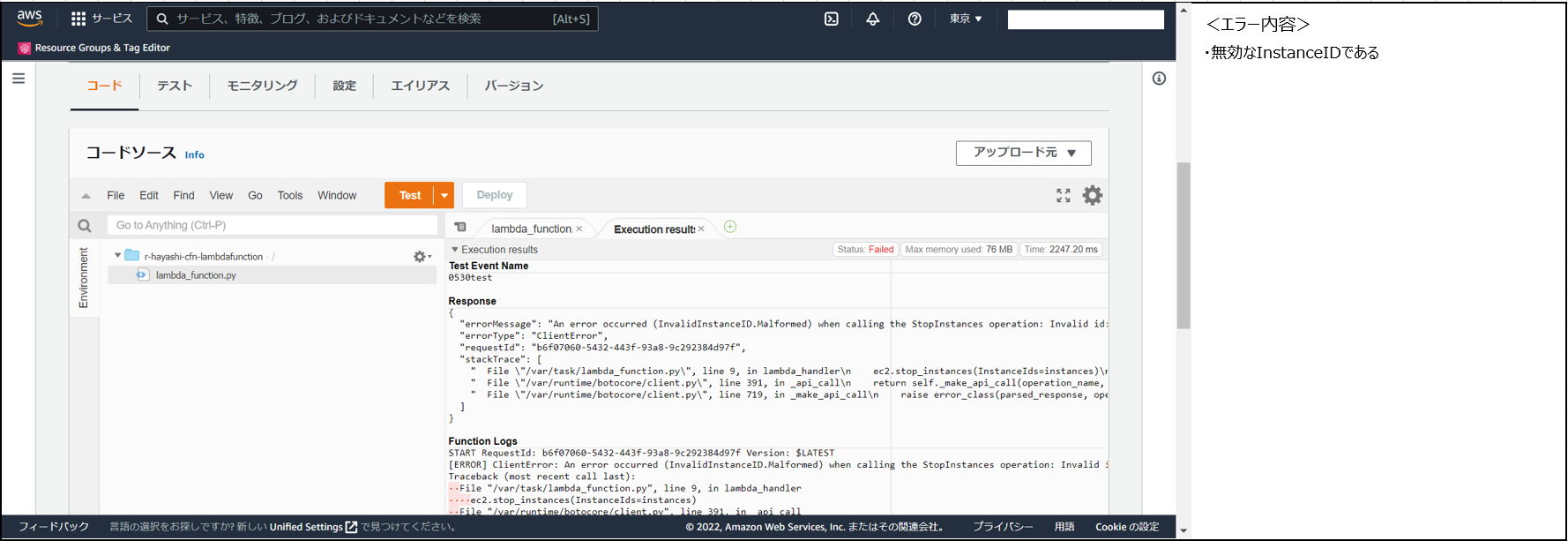
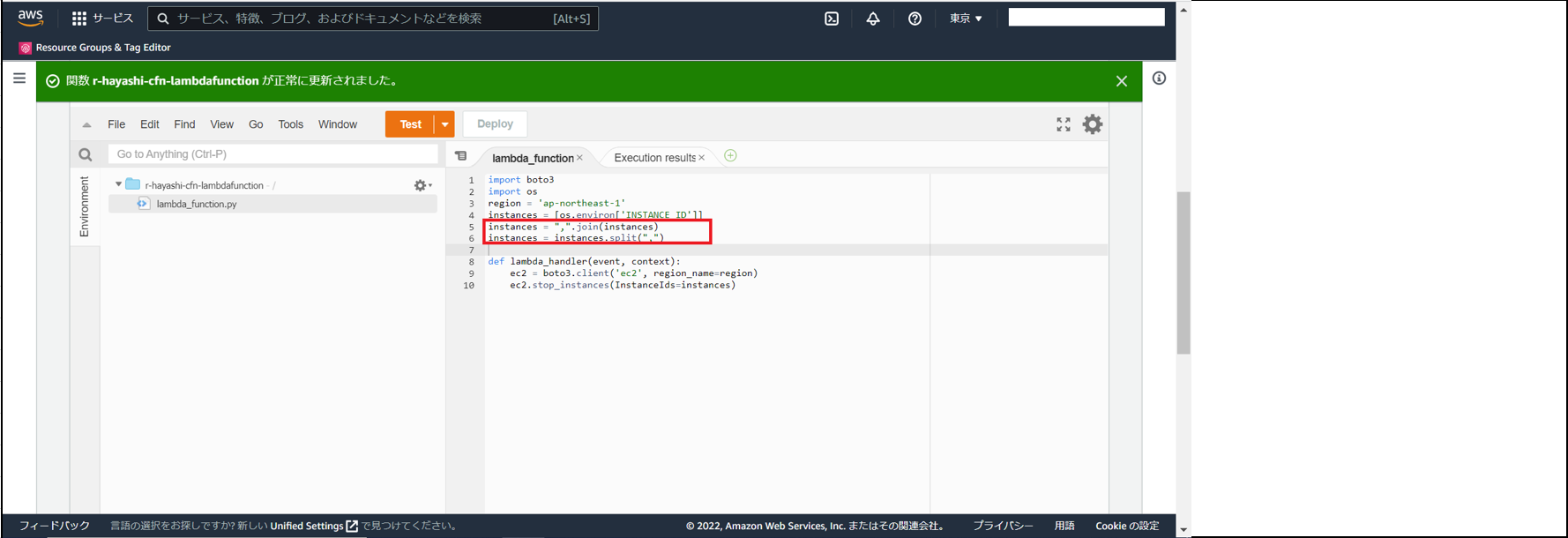
■ 解消
以下画像の通り、pythonファイル内を修正することで解消。
- AWS Configアグリゲータが何度やっても収集されない?
-
■ 実現したいこと
全リージョンでAWS Configを有効化し、ログは単一のS3バケットに集約させたい。
■ 事象
CloudFormationエラーが発生。
■ 解消
S3オブジェクトの所有権を修正することで解消。OwnershipControls: Rules: - ObjectOwnership: BucketOwnerPreferred